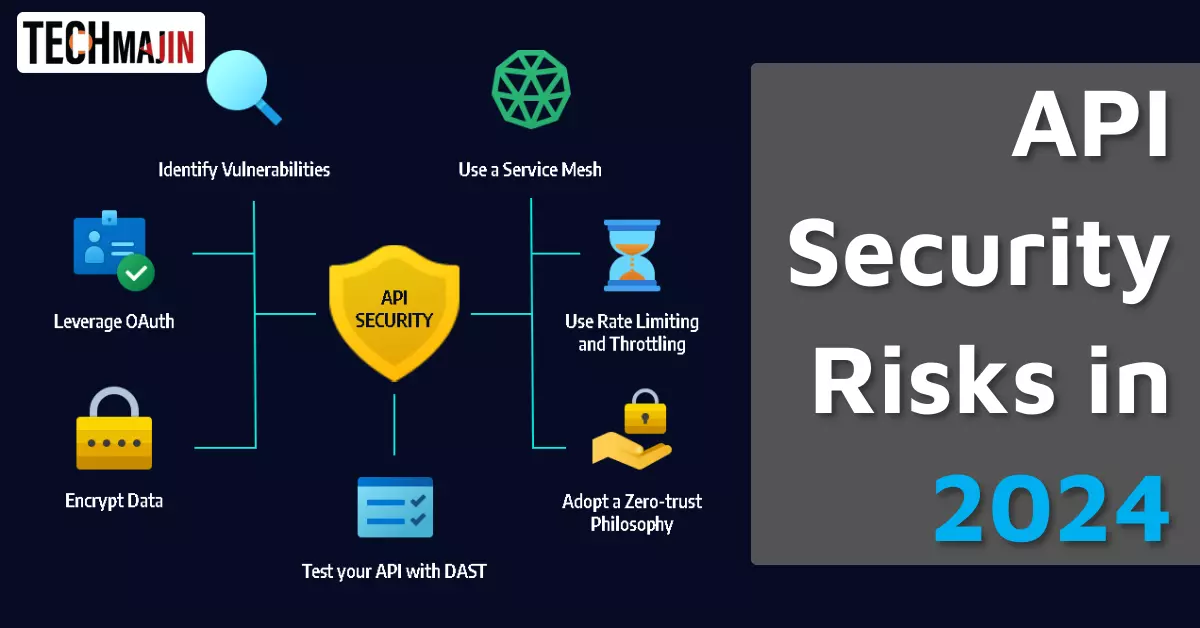
APIs have seamlessly woven themselves into the tapestry of today’s digital environment, enabling interconnected functionalities and data exchanges across disparate systems. However, such open communication comes with significant challenges, primarily revolving around API security and potential vulnerabilities. Safeguarding your digital infrastructure against prevailing API security risks is paramount in an era where digital complexities and cyber threats are continually evolving.
Understanding the Bedrock: APIs
APIs serve as crucial conduits for communication and integration between software applications. Through APIs, applications can share data and functionalities, promoting enhanced user experiences and streamlined operations across various platforms and services. In the interconnected digital realm of 2024, APIs not only facilitate creativity among developers but also bolster business operations by enabling interconnected systems, thereby accentuating their significance in digital infrastructure.
The Imperative Nature of API Security
In this digitally enmeshed world, API security transcends mere best practices and emerges as a critical defense mechanism against potential cyber threats. API security encompasses methodologies and practices designed to shield APIs from unauthorized interference and malicious exploits. A breach in API security could translate to unauthorized data access, massive data breaches, and even a complete systemic compromise, leading to substantial financial losses, brand degradation, and legal implications.
Top 10 API Security Risks to Be Aware Of in 2024
1. Insecure API Endpoints
Depth of Risk:
Data Breaches: Without secure endpoints, APIs can leak data, leading to the exposure of sensitive information like personal data, payment details, or confidential business information.
Unauthorized Access: Insecure endpoints can permit attackers to access secured data repositories or perform unauthorized actions, potentially harming the business or its users.
Exploitation Examples:
Data Leaks: Attackers can exploit insecure endpoints to extract sensitive user information or proprietary data.
Man-in-the-Middle Attacks: Without proper security, attackers can intercept and alter communications between client and server.
2. Lack of Rate Limiting
Depth of Risk:
Service Disruption: A flood of requests can overwhelm the server, disrupting the API service for legitimate users.
Resource Depletion: Exhausting server resources through numerous API calls can degrade overall system performance and availability.
Exploitation Examples:
DDoS Attacks: Cybercriminals might unleash a barrage of requests, aiming to crash the API service or exhaust its resources.
Brute Force Attacks: Attackers might attempt numerous requests to guess credentials, bypassing login mechanisms if no rate limiting is in place.
3. Inadequate Authentication and Authorization
Depth of Risk:
Illegal Access: Weak authentication and authorization mechanisms can lead to unauthorized entities accessing sensitive data.
Data Manipulation: Attackers gaining unauthorized access might manipulate, delete, or corrupt data.
Exploitation Examples:
Privilege Escalation: Attackers can exploit weak authorization to gain elevated access and permissions, potentially allowing them to access or manipulate sensitive data.
Impersonation: Poor authentication can enable attackers to pose as legitimate users, gaining unauthorized access and potentially causing harm.
4. Excessive Data Exposure
Depth of Risk:
Information Disclosure: Unnecessary data exposure can leak valuable information that attackers may utilize to enhance their attack strategies.
Privacy Violation: Exposure of user personal information breaches privacy and may be non-compliant with data protection regulations like GDPR.
Exploitation Examples:
Data Harvesting: Attackers can scrape exposed data, compiling information for future attacks or for sale on the dark web.
Targeted Phishing: Cybercriminals might use the exposed data to construct convincing phishing campaigns, targeting individuals or organizations.
5. Security Misconfigurations
Depth of Risk:
Unintended Exposure: Misconfigurations can inadvertently expose sensitive functionalities or data.
Unauthorized Actions: Inappropriate permissions or exposed functionalities may allow attackers to perform unintended actions on the API.
Exploitation Examples:
Data Exfiltration: If misconfigurations expose data endpoints, attackers might extract data without requiring authentication.
Functionality Abuse: Exposing functionalities, even inadvertently, can let attackers manipulate or utilize these functionalities to cause damage or unauthorized actions.
6. Broken Object Level Security (BOLA/IDOR)
Depth of Risk:
Unauthorized Data Access: Attackers can access and retrieve data they are not permitted to see, leading to potential data breaches.
Data Manipulation: Malicious actors can modify, delete, or corrupt data, disrupting operations and potentially causing harm to users or the organization.
Exploitation Examples:
Data Leak: Through exploiting IDOR vulnerabilities, attackers might access and leak sensitive user data, harming individuals or organizational reputations.
Data Corruption: Attackers may manipulate data objects they aren’t supposed to access, causing issues like incorrect data storage, order manipulation, etc.
7. API Injection Attacks
Depth of Risk:
Data Loss: Injection attacks can lead to unauthorized data retrieval, potentially resulting in data breaches.
Data Corruption: Malicious data inputs can modify or delete database entries, harming data integrity and application functionality.
Exploitation Examples:
Data Breach: SQL injection, for instance, can enable an attacker to access and exfiltrate sensitive data from the database.
Denial of Service: Malicious inputs might corrupt database entries or application data, leading to service disruptions.
8. Inadequate Policy Enforcement
Depth of Risk:
Unauthorized Actions: Lax policies can enable attackers to access functionalities or data outside of their intended scope.
Data Exposure: Weak enforcement of access policies can lead to unauthorized data access, leaks, and potential regulatory non-compliance.
Exploitation Examples:
Data Manipulation: Attackers could exploit weak policies to alter or delete data, harming operations and user experiences.
Service Abuse: Malicious actors might utilize API functionalities in unintended ways, such as sending spam, manipulating data, or disrupting services.
9. Exposing Sensitive Information in API Documentation
Depth of Risk:
Intelligence Gathering: Attackers can utilize detailed API documentation to gain insights into system structures, potential vulnerabilities, and attack vectors.
Enhanced Attack Strategy: The knowledge gained from the documentation enables attackers to formulate more targeted and effective attacks.
Exploitation Examples:
Targeted Attacks: Detailed documentation might expose specific endpoints, methods, or data structures that attackers can directly target.
Vulnerability Exploitation: Knowledge of system functionalities and structures can assist attackers in identifying and exploiting potential weaknesses.
10. API Versioning Issues
Depth of Risk:
Known Vulnerability Exploitation: Older API versions might have unresolved vulnerabilities that attackers are aware of and can exploit.
Data Exposure: Legacy API versions may lack enhanced security measures present in newer versions, leading to potential data leaks.
Exploitation Examples:
Data Breach: Attackers might target older API versions to exploit known vulnerabilities and access sensitive data.
Service Disruption: Exploitation of vulnerabilities in outdated API versions can lead to service outages, affecting user experiences and potentially harming organizational reputation.
Conclusion
In 2024, as digital landscapes continuously evolve, understanding and mitigating API security risks will emerge as a pivotal component in safeguarding digital infrastructures. Proactive approaches towards API security, such as regular auditing, perpetual monitoring, and continuous updates, will significantly mitigate potential risks, safeguarding data, and maintaining system integrity.
While the realm of API interactions offers myriad opportunities for innovation and interconnectivity, it also beckons organizations to prioritize API security, ensuring that their digital operations are not merely prolific but also securely fortified against potential cyber threats.